DarkWeb Markets
Silk Road DeepWeb Drug Market
Silk Road was an online
black market and the first modern
darknet market, best known as a platform for selling illegal drugs. As part of the
dark web,
[6] it was operated as a
Tor hidden service,
such that online users were able to browse it anonymously and securely
without potential traffic monitoring. The website was launched in
February 2011; development had begun six months prior.
[7][8]
Initially there were a limited number of new seller accounts available;
new sellers had to purchase an account in an auction. Later, a fixed
fee was charged for each new seller account.
[9][10]
In October 2013, the
Federal Bureau of Investigation (FBI) shut down the website
[11] and arrested
Ross William Ulbricht under charges of being the site's pseudonymous founder "Dread Pirate Roberts".
[3] On 6 November 2013, Silk Road 2.0 came online, run by former administrators of Silk Road.
[12] It too was shut down, and the alleged operator was arrested on 6 November 2014 as part of the so-called "
Operation Onymous”.
Ulbricht was convicted of eight charges related to Silk Road in
U.S. Federal Court in Manhattan and was sentenced to
life in prison without possibility of parole.
History
Silk Road was founded in February 2011.
[15] The name "Silk Road" comes from a
historical network of trade routes started during the
Han Dynasty
(206 BC – 220 AD) between Europe, India, China, and many other
countries on the Afro-Eurasian landmass. Silk Road was operated by the
pseudonymous "Dread Pirate Roberts" (named after the
fictional character from
The Princess Bride), who was known for espousing
libertarian ideals and criticizing
regulation.
[3][16] Two other individuals were also closely involved in the site's growth and success, known as
Variety Jones and Smedley.
[17]
Henry Farrell,
an associate professor of political science and international affairs
at George Washington University, analyzed Silk Road in an essay for
Aeon in 2015.
[18]
He noted that Ulbricht created the marketplace to function without
government oversight but found it difficult to verify anonymous
transactions. To sustain a steady stream of revenue, he started
increasing oversight to ensure low
transaction costs. To do this, he added measures to ensure trustworthiness with implementation of an automated
escrow payment system and automated review system.
In June 2011,
Gawker published an article about the site
[19] which led to "Internet buzz"
[15] and an increase in website traffic.
[7] Once the site was known publicly, U.S. Senator
Charles Schumer asked federal law enforcement authorities to shut it down, including the
Drug Enforcement Administration (DEA) and
Department of Justice.
[20]
In February 2013, an Australian
cocaine and
MDMA
("ecstasy") dealer became the first person to be convicted of crimes
directly related to Silk Road, after authorities intercepted drugs that
he was importing through the mail, searched his premises, and discovered
his Silk Road alias in an image file on his personal computer.
[21]
Australian police and the DEA have targeted Silk Road users and made
arrests, albeit with limited success at reaching convictions.
[19][22][23]
In December 2013, a New Zealand man was sentenced to two years and four
months in jail after being convicted of importing 15 grams of
methamphetamine that he had bought on Silk Road.
[24]
In May 2013, Silk Road was taken down for a short period of time by a sustained
DDoS attack.
[25] On 23 June 2013, it was first reported that the DEA seized 11.02
bitcoins, then worth $814, which the media suspected was a result of a Silk Road
honeypot sting.
[26][27][28]
The FBI has claimed that the real IP address of the Silk Road server was found via data leaked directly from the site's
CAPTCHA,
[29] but security researchers believe that the
PHP login page was manipulated to output its $_SERVER variable and real IP following site maintenance reconfiguration.
[30]
Arrest and trial of Ross Ulbricht
Image placed on original Silk Road after seizure of property by the
FBI
Impact of the seizure on the USD/Bitcoin exchange rate
Ross Ulbricht
was alleged by the FBI to be the founder and owner of Silk Road and the
person behind the pseudonym "Dread Pirate Roberts" (DPR). He was
arrested on 2 October 2013 in San Francisco
[11][31][32][33] at 3:15 p.m.
PST[34] in
Glen Park Library, a branch of the
San Francisco Public Library.
[34]
Ulbricht was indicted on charges of
money laundering,
computer hacking, conspiracy to traffic narcotics,
[34][35] and attempting to have six people killed.
[36]
Prosecutors alleged that Ulbricht paid $730,000 to others to commit the
murders, although none of the murders actually occurred.
[36] Ulbricht ultimately was not prosecuted for any of the alleged murder attempts.
[37]
The FBI initially seized 26,000 bitcoins from accounts on Silk Road,
worth approximately $3.6 million at the time. An FBI spokesperson said
that the agency would hold the bitcoins until Ulbricht's trial finished,
after which the bitcoins would be liquidated.
[38]
In October 2013, the FBI reported that it had seized 144,000 bitcoins,
worth $28.5 million, and that the bitcoins belonged to Ulbricht.
[39] On 27 June 2014, the
U.S. Marshals Service
sold 29,657 bitcoins in 10 blocks in an online auction, estimated to be
worth $18 million at current rates and only about a quarter of the
seized bitcoins. Another 144,342 bitcoins were kept which had been found
on Ulbricht's computer, roughly $87 million.
[40] Tim Draper
bought the bitcoins at the auction with an estimated worth of $17
million, to lend them to a bitcoin start-up called Vaurum which is
working in developing economies of emerging markets.
[41]
Ulbricht's trial began on 13 January 2015 in Federal Court in
Manhattan.
[42]
At the start of the trial, Ulbricht admitted to founding the Silk Road
website, but claimed to have transferred control of the site to other
people soon after he founded it.
[43] Ulbricht's lawyers contended that Dread Pirate Roberts was really
Mark Karpelès, and that Karpelès set up Ulbricht as a fall guy.
[44] However, Judge
Katherine B. Forrest
ruled that any speculative statements regarding whether Karpelès or
anyone else ran Silk Road would not be allowed, and statements already
made would be stricken from the record.
[45]
In the second week of the trial, prosecutors presented documents and
chat logs from Ulbricht's computer that, they said, demonstrated how
Ulbricht had administered the site for many months, which contradicted
the defense's claim that Ulbricht had relinquished control of Silk Road.
Ulbricht's attorney suggested that the documents and chat logs were
planted there by way of
BitTorrent, which was running on Ulbricht's computer at the time of his arrest.
[45]
On 4 February 2015, the jury convicted Ulbricht of seven charges,
[14]
including charges of engaging in a continuing criminal enterprise,
narcotics trafficking, money laundering, and computer hacking. He faced
30 years to life in prison.
[1][2]
The government also accused Ulbricht of paying for the murders of at
least five people, but there is no evidence that the murders were
actually carried out, and the accusations never became formal charges
against Ulbricht.
[46][47]
During the trial, Judge Forrest received death threats. Users of an underground site called
The Hidden Wiki
posted her personal information there, including her address and Social
Security number. Ulbricht's lawyer Joshua Dratel said that he and his
client "obviously, and as strongly as possible, condemn" the anonymous
postings against the judge. "They do not in any way have anything to do
with
Ross Ulbricht or anyone associated with him or reflect his views or those of anyone associated with him", Dratel said.
[48]
In late March 2015, a criminal complaint issued by the
United States District Court for the Northern District of California led to the arrest of two former federal agents who had worked undercover in the
Baltimore
Silk Road investigation of Ulbricht, former Drug Enforcement
Administration agent Carl Mark Force IV and Secret Service agent Shaun
Bridges.
[49][50]
The agents are alleged to have kept funds that Ulbricht transferred to
them in exchange for purported information about the investigation.
[49][51] The agents were charged with
wire fraud and
money laundering.
[52]
In late November 2016, Ulbricht's lawyers brought forward a case on a
third DEA agent, who they claim was leaking information about the
investigation and tampered with evidence to omit chat logs showing
conversations with him.
[53]
On March 15, 2015, director/screenwriter
Alex Winter debuted at the
South by Southwest Film Festival a movie based on Silk Road.
Deep Web gives the inside story of the arrest of Ross Ulbricht.
[54]
In a letter to Judge Forrest before his sentencing, Ulbricht stated that his actions through Silk Road were committed through
libertarian
idealism and that "Silk Road was supposed to be about giving people the
freedom to make their own choices" and admitted that he made a
"terrible mistake" that "ruined his life".
[55][56] On May 29, 2015, Ulbricht was given five
sentences to be served concurrently, including two for
life imprisonment without the possibility of
parole.
[57] He was also ordered to
forfeit $183 million. Ulbricht’s lawyer Joshua Dratel said that he would
appeal the sentencing and the original guilty verdict.
[46].
On May 31, 2017, the United States Court of Appeals for the Second
Circuit denied Ulbricht's appeal, and affirmed the judgment of
conviction and life sentence, in a written opinion authored by the
Honorable
Gerard E. Lynch, United States Circuit Judge.
[58]
Products
In March 2013, the site had 10,000 products for sale by vendors, 70% of which were drugs.
[19][65] In October 2014, there were 13,756 listings for drugs, grouped under the headings
stimulants,
psychedelics,
prescription,
precursors, other,
opioids,
ecstasy,
dissociatives, and
steroids/
PEDs.
[7][15][66][67] Fake driver's licenses were also offered for sale.
[68]
The site's terms of service prohibited the sale of certain items. When
the Silk Road marketplace first began the creator and administrators
instituted terms of service that prohibited the sale of anything whose
purpose was to "harm or defraud".
[15][69] This included
child pornography, stolen credit cards, assassinations, and weapons of any type; other darknet markets such as
Black Market Reloaded gained user notoriety because they were not as restrictive on these items as the Silk Road incarnations were.
[65][70] There were also legal goods and services for sale, such as
apparel,
art,
books,
cigarettes,
erotica,
jewelery,
and writing services. A sister site, called "The Armory", sold weapons
(primarily guns) during 2012, but was shut down because of a lack of
demand.
[71][72]
Buyers were able to leave reviews of sellers' products on the site, and in an associated forum where
crowdsourcing provided information about the best sellers and worst scammers.
[73]
Most products were delivered through the mail, with the site's seller's
guide instructing sellers how to vacuum-seal their products to escape
detection.
[74]
Sales
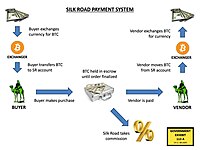
A
flowchart depicting Silk Road's payment system.
Exhibit 113 A, entered into evidence at Ulbricht's trial.
Based on data from 3 February 2012 to 24 July 2012, an estimated $15 million in transactions were made annually on Silk Road.
[75][76]
Twelve months later, Nicolas Christin, the study's author, said in an
interview that a major increase in volume to "somewhere between $30
million and $45 million" would not surprise him.
[77] Buyers and sellers conducted all transactions with bitcoins (BTC), a
cryptocurrency that provides a certain degree of
anonymity.
[78] Silk Road held buyers' bitcoins in
escrow until the order had been received and a
hedging mechanism
allowed sellers to opt for the value of bitcoins held in escrow to be
fixed to their value in US$ at the time of the sale to mitigate against
Bitcoin's volatility. Any changes in the price of bitcoins during
transit were covered by Dread Pirate Roberts.
[79]
The
complaint published when Ulbricht was arrested included information the FBI gained from a
system image
of the Silk Road server collected on 23 July 2013. It noted that, "From
February 6, 2011 to July 23, 2013 there were approximately 1,229,465
transactions completed on the site. The total revenue generated from
these sales was 9,519,664 Bitcoins, and the total commissions collected
by Silk Road from the sales amounted to 614,305 Bitcoins. These figures
are equivalent to roughly $1.2 billion in revenue and $79.8 million in
commissions, at current Bitcoin exchange rates...", according to the
September 2013 complaint, and involved 146,946 buyers and 3,877 vendors.
[11]
This statement was made to emphasize the importance of the operation,
because in the years 2011-2013 the value of 9,519,664 Bitcoins was $0.2
billion.
[80]
According to information users provided upon registering, 30 percent
were from the United States, 27 percent chose to be "undeclared", and
beyond that, in descending order of prevalence: the United Kingdom,
Australia, Germany, Canada, Sweden, France, Russia, Italy, and the
Netherlands. During the 60-day period from 24 May to 23 July, there were
1,217,218 messages sent over Silk Road's private messaging system.
[11]